Your Dedicated Partner in
Complete Web Protection
Your Dedicated Partner in
Complete Web Protection
Your Dedicated Partner in Complete Web Protection
Explore state-of-the-art approaches for inclusive data protection, guaranteeing a secure and defended digital environment.
Explore state-of-the-art approaches for inclusive data protection, guaranteeing a secure and defended digital environment.
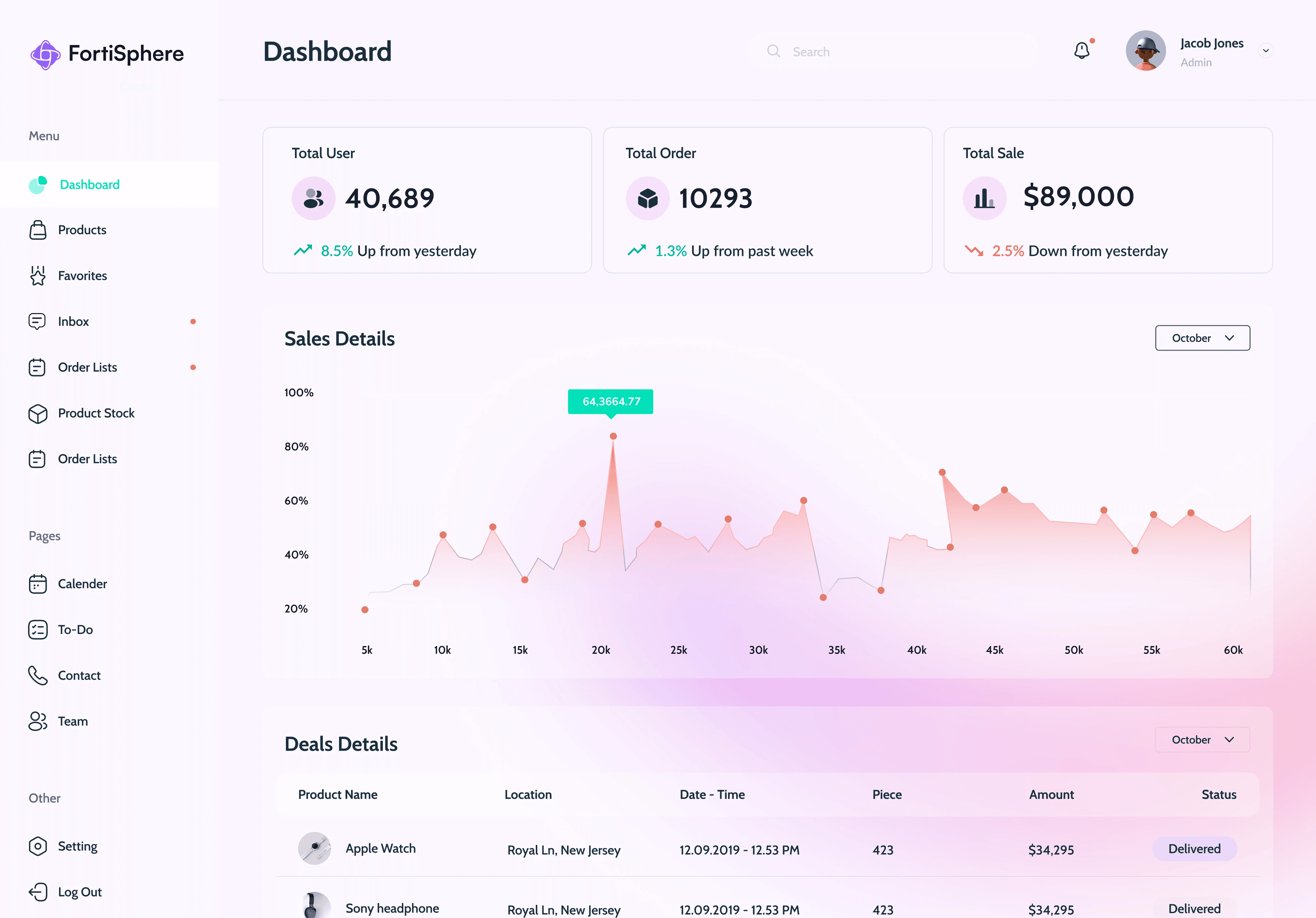


Securing Your Digital World:
Securing Your Digital World:
Securing Your Digital World:

HOW IT WORKS
HOW IT WORKS
HOW IT WORKS
The operation of Clarity's
Security System
The operation of Clarity's
Security System
The operation of Clarity's
Security System
The operation of
Clarity's Security System
Safeguarding your online universe: your reliable ally in information safeguard with pioneering tactics for exhaustive data safety.
Safeguarding your online universe: your reliable ally in information safeguard with pioneering tactics for exhaustive data safety.
Safeguarding your online universe: your reliable ally in information safeguard with pioneering tactics for exhaustive data safety.
Advanced Detection
Advanced Detection
Our platform ceaselessly scrutinizes your network and data milieu for prompt identification of any anomalous actions.
Our platform ceaselessly scrutinizes your network and data milieu for prompt identification of any anomalous actions.
Advanced Detection
Our platform ceaselessly scrutinizes your network and data milieu for prompt identification of any anomalous actions.
Robust Data Encryption
Robust Data Encryption
Rest assured, all sensitive data is encrypted during transfer and storage using widely accepted encryption techniques.
Rest assured, all sensitive data is encrypted during transfer and storage using widely accepted encryption techniques.
Robust Data Encryption
Rest assured, all sensitive data is encrypted during transfer and storage using widely accepted encryption techniques.
Automatic Updates
Automatic Updates
In a security breach situation, our automation based reaction mechanism rapidly triggers defensive actions.
In a security breach situation, our automation based reaction mechanism rapidly triggers defensive actions.
Automatic Updates
In a security breach situation, our automation based reaction mechanism rapidly triggers defensive actions.
Cost Efficiency
Cost Efficiency
Should a security episode occur, our autopilot defense mechanism swiftly triggers safeguarding actions.
Should a security episode occur, our autopilot defense mechanism swiftly triggers safeguarding actions.
Cost Efficiency
Should a security episode occur, our autopilot defense mechanism swiftly triggers safeguarding actions.
Enhanced Security
Enhanced Security
Our platform persistently scrutinizes your network and data terrain to immediately identify any questionable movements.
Our platform persistently scrutinizes your network and data terrain to immediately identify any questionable movements.
Enhanced Security
Our platform persistently scrutinizes your network and data terrain to immediately identify any questionable movements.
Scalability & Flexibility
Scalability & Flexibility
You can feel confident that critical data retains its protection during transmission and storage, utilizing methods consistent with international encryption norms.
You can feel confident that critical data retains its protection during transmission and storage, utilizing methods consistent with international encryption norms.
Scalability & Flexibility
You can feel confident that critical data retains its protection during transmission and storage, utilizing methods consistent with international encryption norms.
SECURITY
SECURITY
Comprehensive Overview of Our Internet Safety Capabilities
Comprehensive Overview of Our Internet Safety Capabilities
Comprehensive Overview of
Our Internet Safety Capabilities
Guarding your virtual universe: your reliable ally in information safeguarding with advanced methods for thorough data protection.
Guarding your virtual universe: your reliable ally in information safeguarding with advanced methods for thorough data protection.
Guarding your virtual universe: your reliable ally in information safeguarding with advanced methods for thorough data protection.
18%
30-45 years
46%
18-30 years
18%
30-45 years
Visitor History
Visitor History
Visitor History
Visitor History
Continuously assesses potential security threats
Continuously assesses potential security threats
Continuously assesses potential security threats
Safeguarding your cyber space: your reputable ally in preserving information.
Safeguarding your cyber space: your reputable ally in preserving information.
Safeguarding your cyber space: your reputable ally in preserving information.
18%
30-45 years
46%
18-30 years
18%
30-45 years
Visitor History
Visitor History
Continuously assesses potential security threats
Safeguarding your cyber space: your reputable ally in preserving information.
May
May
Jun
Jun
Jul
Jul
Aug
Aug
Sep
Sep
Oct
Oct
Now
Now
Sale Data
Sale Data
Sale Data
Sale Data
Continually evaluates possible security risks
Continually evaluates possible security risks
Continually evaluates possible security risks
Safeguarding your online universe: your reliable ally in preserving data.
Safeguarding your online universe: your reliable ally in preserving data.
Safeguarding your online universe: your reliable ally in preserving data.
May
Jun
Jul
Aug
Sep
Oct
Now
Sale Data
Sale Data
Continually evaluates possible security risks
Safeguarding your online universe: your reliable ally in preserving data.
Jan
Jan
Feb
Feb
Mar
Mar
Apr
Apr
May
May
Jun
Jun
Contextual Banners
Contextual Banners
Clicks
Without Transition
With Transaction
Banners clicks
Banners clicks
Monitors and logs each instance of data access
Monitors and logs each instance of data access
Monitors and logs each instance of data access
Safeguarding your virtual universe: your reliable ally in securing information with
Safeguarding your virtual universe: your reliable ally in securing information with
Safeguarding your virtual universe: your reliable ally in securing information with
Jan
Feb
Mar
Apr
May
Jun
Contextual Banners
Clicks
Without Transition
With Transaction
Banners clicks
Monitors and logs each instance of data access
Safeguarding your virtual universe: your reliable ally in securing information with
KEY FEATURES
KEY FEATURES
Explore the Traits That Make Fortify Distinguished.
Explore the Traits That Make Fortify Distinguished.
Explore the Traits That
Make Fortify Distinguished.
Protecting your digital world: your reliable partner in comprehensive data security solutions.
Protecting your digital world: your reliable partner in comprehensive data security solutions.
Protecting your digital world: your reliable partner in comprehensive
data security solutions.
ORGANIC SEARCH
1,360
1,360
25%
REFERRAL
2,605
2,605
46%
992
992
25%
SOCIAL MEDIA
1,032
1,032
14%
Sessions By Channel
In-Depth Explanation of Our Web Security
In-Depth Explanation of Our Web Security
In-Depth Explanation of Our Web Security
Safeguarding Your Online Universe: Your Reliable Ally in Information Security Utilizing State-of-the-Art Answers for
Safeguarding Your Online Universe: Your Reliable Ally in Information Security Utilizing State-of-the-Art Answers for
Erased user trails
Our system consistently records all user actions, including sign-ins.
Our system consistently records all user actions, including sign-ins.
Our system consistently records all user actions, including sign-ins.
User routes sketcher
This entails strange sign-in instances and entry to confined records.
This entails strange sign-in instances and entry to confined records.
This entails strange sign-in instances and entry to confined records.
ORGANIC SEARCH
1,360
25%
REFERRAL
2,605
46%
992
25%
SOCIAL MEDIA
1,032
14%
Sessions By Channel
In-Depth Explanation of Our Web Security
Safeguarding Your Online Universe: Your Reliable Ally in Information Security Utilizing State-of-the-Art Answers for
Erased user trails
Our system consistently records all user actions, including sign-ins.
User routes sketcher
This entails strange sign-in instances and entry to confined records.
Presents a Comprehensive Safety Overview.
Presents a Comprehensive Safety Overview.
Presents a Comprehensive Safety Overview.
Delivering secure strength
Delivering secure strength
Delivering secure strength
Apply Dual-Stage Authentication
Apply Dual-Stage Authentication
Apply Dual-Stage Authentication
Persistently verify user authorizations
Persistently verify user authorizations
Persistently verify user authorizations
Shielding your online realm
Shielding your online realm
Shielding your online realm
Get Start
Get Start
Get Start
Get Start
Delivered
15 new packages
15 new packages
Ordered
15 new packages
15 new packages
Reported
15 new packages
15 new packages
Arrived
15 new packages
15 new packages
Activity
Check out each collumn for more details
Customer Reviews
Customer Reviews
Securing your digital world: your trusted partner in data protection with
cutting-edge solutions
Securing your digital world: your trusted partner in data protection with cutting-edge solutions
Securing your digital world: your trusted partner in data protection with cutting-edge solutions
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.
4.9

Michael Brown
IT Director at HealthCare
FortiSphere
Subscribe to Our Newsletter!
Stay Informed with Our Latest Security Insights - Subscribe to Our Newsletter!
© 2025 FortiSphere. Made by Annie Fam
FortiSphere
Subscribe to Our Newsletter!
Stay Informed with Our Latest Security Insights - Subscribe to Our Newsletter!
© 2025 FortiSphere. Made by Annie Fam
FortiSphere
Subscribe to Our Newsletter!
Stay Informed with Our Latest Security Insights - Subscribe to Our Newsletter!
© 2025 FortiSphere. Made by Annie Fam
FortiSphere
Subscribe to Our Newsletter!
Stay Informed with Our Latest Security Insights - Subscribe to Our Newsletter!
© 2025 FortiSphere. Made by Annie Fam





